Introducing the New CISA Threat Sandbox Challenges!
Today, we are thrilled to unveil and introduce our latest set of Challenges, the CISA Threat Sandbox Challenges! Over the past year, we have had the privilege of collaborating with the Cybersecurity and Infrastructure Security Agency (CISA) to develop twelve (12) hands-on purple team (combination of red and blue teams) style cyber challenge exercises.
Each CISA Threat Sandbox Challenge revolves around a Common Vulnerability & Exposure (CVE) that has been included in the CISA Known Exploited Vulnerabilities (KEV) Catalog. Participants are provided with authoritative sources of information related to the chosen CVE and are tasked with using their offensive and defensive cyber skills to accomplish two objectives: one red team (e.g., exploit and exfiltrate, exploit and deploy C2-enabled malware, etc.) and one blue team (e.g., patch vulnerable software, implement mitigations, etc.). The participant will complete these objectives in a virtual environment that includes systems tailored to the needs of the CVE and contextualized as systems being used by organizations and businesses within a critical infrastructure (CI) sector.
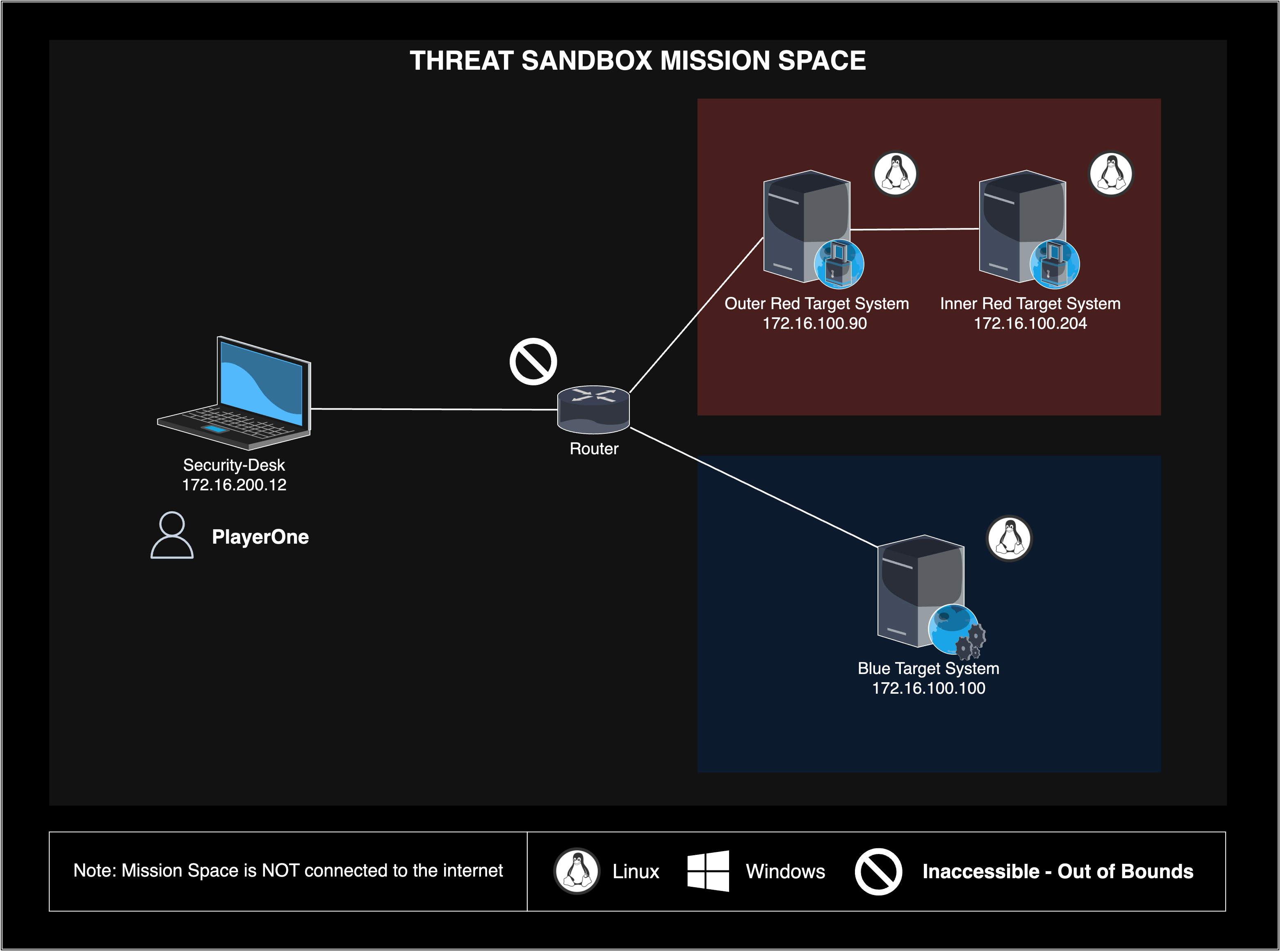
Below you can see the virtual environment network map for the CISA Threat Sandbox Challenge: Apache Proxy4All (CVE-2021-40438).
CISA Threat Sandbox Challenge Highlights
As mentioned earlier, we are launching twelve (12) CISA Threat Sandbox Challenges. We highly recommend that you explore all of them on the NICE Challenge Webportal or XP Cyber Range (Curator Account Required). Below, we have highlighted two of these challenges to give you a glimpse of what to expect.
CISA Threat Sandbox Challenge: UnRAR v Zimbra (CVE-2022-30333)
In this CISA Threat Sandbox Challenge the participant will learn about CVE-2022-30333, a seemingly unassuming directory traversal and arbitrary write vulnerability in a simple file extracting application, and then exercise that knowledge along with their offensive and defensive cyber skills. After learning about the CVE, they will be asked to complete two technical objectives, one red team (offensive) and one blue team (defensive), related to the CVE:
- Red Team (Offensive) Objective: Utilize CVE-2022-30333 to start a multi-step exploit chain to deploy command and control (C2) enabled malware on a system running a vulnerable UnRAR version as part of a Zimbra Collaboration Suite instance used by an information technology (IT) business (i.e., the red target system).
- Blue Team (Defensive) Objective: Patch CVE-2022-30333 to safeguard a system running a Zimbra Collaboration Suite instance used by an information technology (IT) business (i.e., the blue target system).
CISA Threat Sandbox Challenge: Apache Proxy4All (CVE-2021-40438)
In this CISA Threat Sandbox Challenge the participant will learn about CVE-2021-40438, a dangerous server-side request forgery (SSRF) vulnerability, and then exercise that knowledge along with their offensive and defensive cyber skills. After learning about the CVE, they will be asked to complete two technical objectives, one red team (offensive) and one blue team (defensive), related to the CVE:
- Red Team (Offensive) Objective: Utilize CVE-2021-40438 to exploit a vulnerable Apache web server-based remote site VPN appliance (i.e., the outer red target system) to perform recon on a typically externally inaccessible ICS/OT system (i.e., the inner red target system), where all of the involved systems are operated by an energy utility company.
- Blue Team (Defensive) Objective: Patch CVE-2021-40438 on a vulnerable Apache web server-based remote site VPN appliance (i.e., the blue target system) to safeguard the ICS/OT network the appliance guards access to, where all of the involved systems are operated by an energy utility company.

This environment and challenges were created through a partnership with and funding provided by CISA.
