Introducing the New Protect & Defend Environment and Challenges!
Today we wanted to fully announce our newest environment, crafted for challenges within the Protect & Defend category of the NICE Framework.
This environment has taken months of designing, planning, and engineering to create. We are proud to call it our latest work and can’t wait to have our players and curators completing challenges in this new environment. Now, let’s get into the details!
– – PROTECT & DEFEND ENVIRONMENT – –
The NICE Challenge Team would like to invite you into our Protect & Defend environment, Pretty Safe Electronics!

Pretty Safe Electronics, or PSE, is a local big box retailer that primarily sells electronics. The environment was designed to host challenges derived from tasks and work roles within the Protect & Defend category of the NICE Framework. In contrast to the relatively flat network of the Operate & Maintain environment, Protect & Defend features six isolated layer two networks woven together with routing appliances and site-to-site VPN tunnels. With its two remote retail locations, POS terminals, and self-hosted e-commerce website, there are diverse potential attack surfaces supporting a wide variety of challenges where players can engage active threats.
We cannot wait to see players and curators in the Protect & Defend environment attempting challenges and experiencing narratives told through the diverse new cast of characters working at PSE!
– – PROTECT & DEFEND CHALLENGE HIGHLIGHTS – –
At present, there are already ten challenges available within the new environment. While we encourage you to take a look at them all on the Webportal (assuming you have a curator account), we are going to highlight two of the ten challenges here to give you a taste of what you can expect to find in this new environment.
Challenge: Malware Aftermath Cleanup
Being a small retailer and having limited funding for technical staff, PSE contracts with a managed service provider (MSP) to do some systems management and upkeep. Unfortunately, this expands the pool of people who have high-level access to business-critical systems. In this challenge, the MSP’s access is misused by a rogue employee to implant some custom-made malware for purposes unknown. The player is told to review some suspicious looking traffic on the main firewall and from there they must identify the compromised system, quarantine the malware, and oust the rogue former MSP employee from the system.
Challenge: Incoming Zero Day! Prepare the IDS/IPS!
In this challenge, PSE’s MSP has contacted Ashley Steele, the Sr. Systems Engineer, and notified her of a new exploit that targets PSE’s e-commerce platform. The MSP has provided PSE with a string present in the malicious web requests issued by the exploit. The player must craft a custom IDS rule using the provided string and implement that rule on the Snort installation on the main firewall, so that PSE’s staff will be made aware when malicious traffic arrives.
This environment has taken months of designing, planning, and engineering to create. We are proud to call it our latest work and can’t wait to have our players and curators completing challenges in this new environment. Now, let’s get into the details!
The NICE Challenge Team would like to invite you into our Protect & Defend environment, Pretty Safe Electronics!
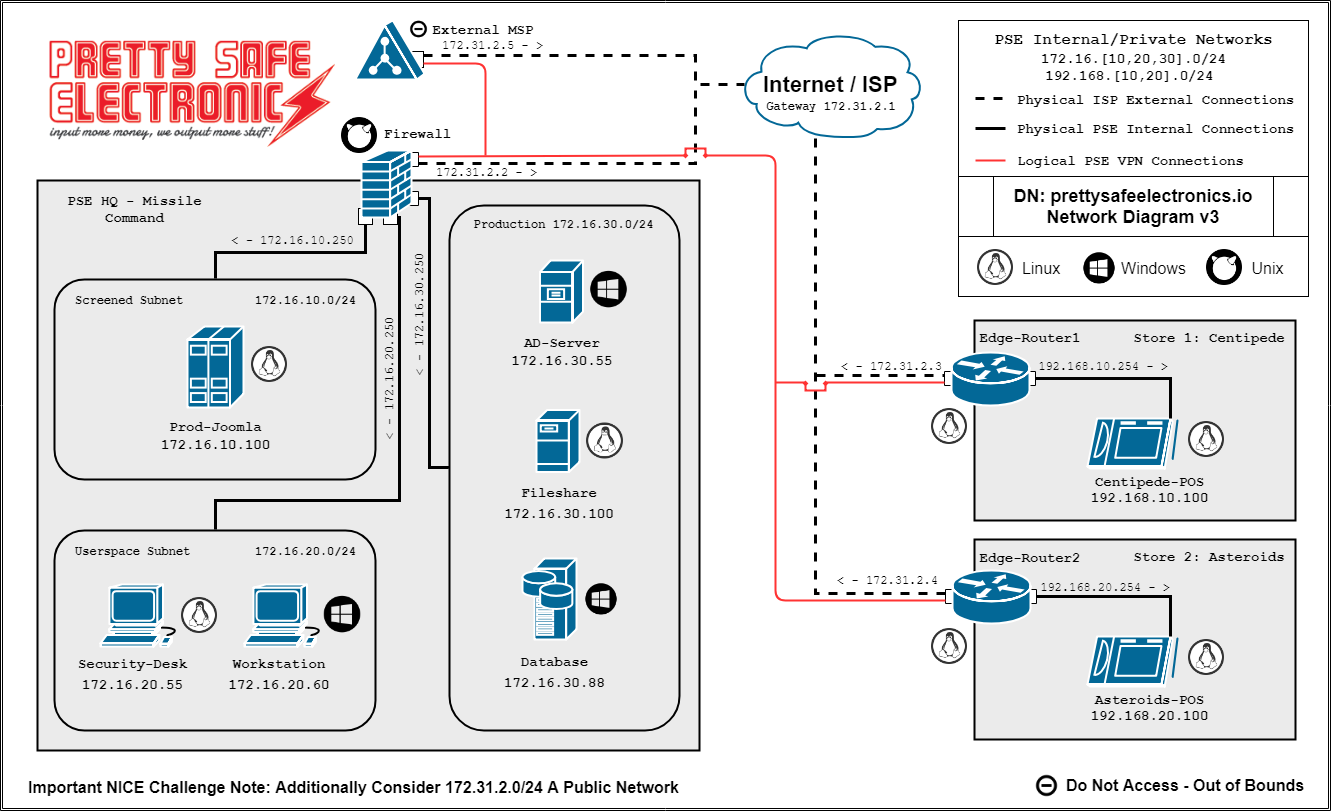
Pretty Safe Electronics, or PSE, is a local big box retailer that primarily sells electronics. The environment was designed to host challenges derived from tasks and work roles within the Protect & Defend category of the NICE Framework. In contrast to the relatively flat network of the Operate & Maintain environment, Protect & Defend features six isolated layer two networks woven together with routing appliances and site-to-site VPN tunnels. With its two remote retail locations, POS terminals, and self-hosted e-commerce website, there are diverse potential attack surfaces supporting a wide variety of challenges where players can engage active threats.
We cannot wait to see players and curators in the Protect & Defend environment attempting challenges and experiencing narratives told through the diverse new cast of characters working at PSE!
At present, there are already ten challenges available within the new environment. While we encourage you to take a look at them all on the Webportal (assuming you have a curator account), we are going to highlight two of the ten challenges here to give you a taste of what you can expect to find in this new environment.
Challenge: Malware Aftermath Cleanup
Being a small retailer and having limited funding for technical staff, PSE contracts with a managed service provider (MSP) to do some systems management and upkeep. Unfortunately, this expands the pool of people who have high-level access to business-critical systems. In this challenge, the MSP’s access is misused by a rogue employee to implant some custom-made malware for purposes unknown. The player is told to review some suspicious looking traffic on the main firewall and from there they must identify the compromised system, quarantine the malware, and oust the rogue former MSP employee from the system.
Challenge: Incoming Zero Day! Prepare the IDS/IPS!
In this challenge, PSE’s MSP has contacted Ashley Steele, the Sr. Systems Engineer, and notified her of a new exploit that targets PSE’s e-commerce platform. The MSP has provided PSE with a string present in the malicious web requests issued by the exploit. The player must craft a custom IDS rule using the provided string and implement that rule on the Snort installation on the main firewall, so that PSE’s staff will be made aware when malicious traffic arrives.
